
What Is the Digital Operational Resilience Act (DORA)?
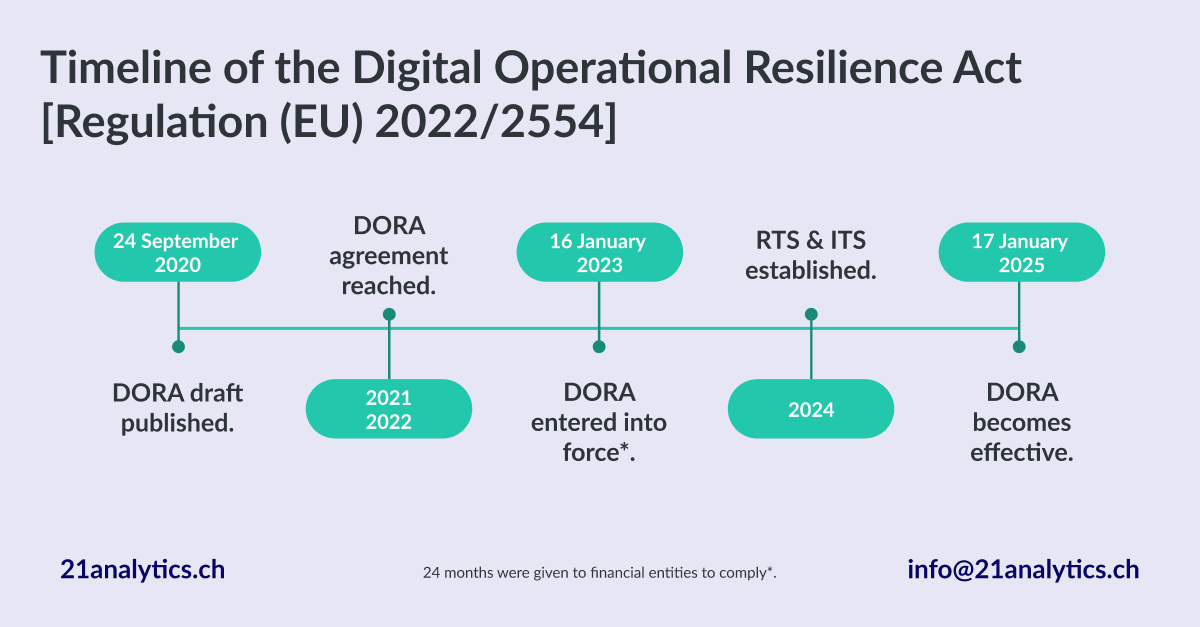
The Digital Operational Resilience Act (Regulation (EU) 2022/2554), known as DORA was first drafted on 24 September 2020 with the final version becoming effective on 17 January 2025*.
DORA forms part of the Digital Finance Package and covers European Union (EU) financial institutions and associated information and communication technology (ICT) service providers.
*DORA requirements are enforceable 24 months after entry into force (16th January 2023).
What Are DORA’s Objectives?
DORA has 2 main objectives: strengthening financial sectors’ resilience to ICT-related incidents and harmonising existing risk management regulations within the EU. DORA achieves this by providing a specific set of criteria, templates and instructions that will shape how financial organisations manage ICT and cyber risks.
By harmonising risk management rules across the EU, DORA seeks to eliminate any gaps, overlapping issues, and conflicts that could arise between contrasting regulations in different EU states. Financial entities can comply more easily with a single set of rules, ultimately improving the entire EU financial system's robustness by ensuring that every institution abides by the same standard.
What Falls under DORA’s Scope?
DORA applies to all financial institutions in the EU. This includes traditional financial entities such as banks, investment firms, and credit institutions, as well as non-traditional entities such as crypto-asset service providers (CASPs) and crowdfunding platforms*.
*For the exhaustive list, please refer to Article 2 of the Digital Operational Resilience Act (Regulation (EU) 2022/2554),
What Isn’t Covered by DORA?
DORA is not applicable to:
“(a) managers of alternative investment funds as referred to in Article 3(2) of Directive 2011/61/EU;
(b) insurance and reinsurance undertakings as referred to in Article 4 of Directive 2009/138/EC;
(c) institutions for occupational retirement provision which operate pension schemes which together do not have more than 15 members in total;
(d) natural or legal persons exempted pursuant to Articles 2 and 3 of Directive 2014/65/EU; (e) insurance intermediaries, reinsurance intermediaries and ancillary insurance intermediaries which are microenterprises or small or medium-sized enterprises;
(f) post office giro institutions as referred to in Article 2(5), point (3), of Directive 2013/36/EU.”*
*For the exhaustive list, please refer to Article 2 of the Digital Operational Resilience Act (Regulation (EU) 2022/2554)
DORA’s Timeline:
2020: On 24 September 2020, the EU Commission introduced the draft version of DORA as part of its Digital Finance Package (DFP).
2021 / 2022: An agreement was reached.
After the European Parliament and Council published their proposals for DORA, co-legislators engaged in discussions throughout the first half of 2022. The European Parliament approved the act on 10 November 2022, and the European Council adopted it on 28 November 2022.
2023: DORA entered into force on 16 January 2023 and serves to complement the existing NIS and GDPR legislation.
2024: Regulatory Technical Standard (RTS) & Implementation Technical Standard (ITS).
The European Supervisory Authorities (ESAs) establish and issue various regulatory and implementing technical standards with detailed specifications and guidance for meeting DORA’s requirements.
[ESAs include the EBA, EIOPA, and ESMA, which are responsible for developing technical standards for financial institutions to abide by].
2025: Enforcement.
DORA will be effective on 17 January 2025. While enforced on 16 January 2023, 24 months were given to financial entities to comply with DORA’s requirements.
What Are DORA’s 5 Pillars?
ICT Risk Management: Chapter II (Articles 5 - 16)
DORA requires a robust ICT risk management framework, mandating the use of resilient systems and tools to mitigate risks, continuous identification of ICT threats, and prompt detection of anomalies.
Entities are responsible for developing comprehensive business continuity and disaster recovery plans to ensure rapid recovery from ICT incidents. DORA mandates that the management body, including board members and senior managers are responsible for ICT risk management. These parties must define strategies, support implementation, and stay informed about the risk landscape. Strategies include establishing detailed ICT risk management frameworks, mapping their systems, classifying assets, conducting ongoing risk assessments, and implementing cybersecurity measures.
Additionally, they must perform business impact analyses, set risk tolerance levels, and deploy technical controls such as extended detection and response systems. Business continuity and disaster recovery plans must cover data backup, system restoration, and communication protocols.
Upcoming Regulatory Technical Standards (RTSs) will outline the necessary components of the risk management framework, which are in line with existing EBA guidelines.
ICT-related Incident Reporting: Chapter III (Articles 17, 23 and 24)
It is important to prevent the impact of ICT-related incidents and, if detected, manage them accordingly. Entities are responsible for implementing systems that monitor, manage, log, classify, and report these, following criteria established by the relevant ESAs.
Incidents must be reported to relevant authorities using a standardised template and coordinated procedures, including the submission of initial, intermediate, and final reports to regulators, affected clients, and partners.
Digital Operational Resilience Testing
Entities must regularly run tests to assess the security of their IT systems and centres. DORA mandates companies to develop risk-oriented programs address and improve its digital resilience.
Managing of ICT Third-party Risk: Chapter V (Articles 28 - 44)
DORA states that entities must ensure effective risk monitoring associated with ICT third-party providers by standardising key aspects of service and relationships, including detailed contracts that specify service levels and data processing locations.
Moreover, financial firms must manage third-party risks by negotiating specific contractual arrangements covering exit strategies, audits, and performance targets for accessibility, integrity, and security.
DORA prohibits contracts with non-compliant ICT providers; in fact, competent authorities can suspend or terminate such an agreement. To ensure compliance, the European Commission is considering standardised contractual clauses.
Relevant ESAs will directly oversee critical ICT providers, enforcing DORA requirements and preventing non-compliant contracts.
Information Sharing
Financial entities must implement processes to learn from internal and external ICT-related incidents. To support this, DORA encourages participation in voluntary threat intelligence sharing arrangements, with the requirement that shared information is protected under relevant guidelines, such as GDPR for personally identifiable information.
DORA also urges entities to collaborate with trusted communities to improve digital operational resilience, raise awareness of ICT risks, and enhance defensive, detection, and response strategies. Lastly, the secure exchange of cyber threat information and intelligence is promoted to ensure sensitive data remains protected.
21 Travel Rule Minimises ICT-related Risks
With DORA’s stringent requirements, CASPs must consider the impact of their Travel Rule providers on their business.
One of DORA’s main objectives is to strengthen the financial sector’s resilience to ICT-related incidents. Therefore, it makes sense for CASPs to implement an on-premises (on-prem) Travel Rule solution.
Many customers of SaaS products mistakenly believe that opting for SaaS eliminates numerous risks related to backup, uptime, and security. In reality, these risks are transferred to a third party, where incidents can still arise. On-prem solutions drastically reduce the risk of data breaches, have decreased attack surfaces, and create less complexity than their SaaS counterparts.
21 Travel Rule is an on-premises solution, which means zero data is shared with a third party (us), maximising data protection and privacy while reducing ICT risks.
Find out more about 21 Travel Rule.


